How does credential stuffing work?
A credential stuffing attack involves fraudulently obtaining valid account credentials (e.g., pairs of usernames/email addresses and passwords) obtained from compromised accounts on third-party services and “stuffing” these into the account log-in sections of online sites until correct matches are found. The attacks are relatively straightforward to launch via automated software (e.g., account checker apps), which can attempt to access large numbers of accounts at great speed.
Why are credential stuffing attacks carried out?
The primary motivation for this type of cyberattack is financial gain; however, attackers may also seek to cause more intangible harm to the account holder. Such harm may include leaking sensitive personal information, causing reputational damage or infiltrating business accounts.
Such attacks exploit both vulnerabilities in human nature around security (for example the fact that individuals still regularly use the same username and password for different accounts) and technical failings, which can result in security incidents leaking credentials for purchase or general use by attackers.
What is the relevant existing law in this area and the status of these Guidelines?
Whilst it is true that the credentials used in such attacks may be accessed due to faults on the part of users or services they are taken from originally, the service that is the victim of the attack also has obligations under data protection laws to take measures to help detect, prevent and mitigate the risk of the attack. Such security obligations are usually framed in high-level terms. For example, in the UK and Europe, the General Data Protection Regulation specifies that organisations should process data in a manner that “ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss…” The Safeguards Rule in the USA refers to the implementation of “administrative, technical, and physical safeguards that are appropriate to your size and complexity, the nature and scope of your activities, and the sensitivity of the customer information at issue…” and that “protect against unauthorised access”.
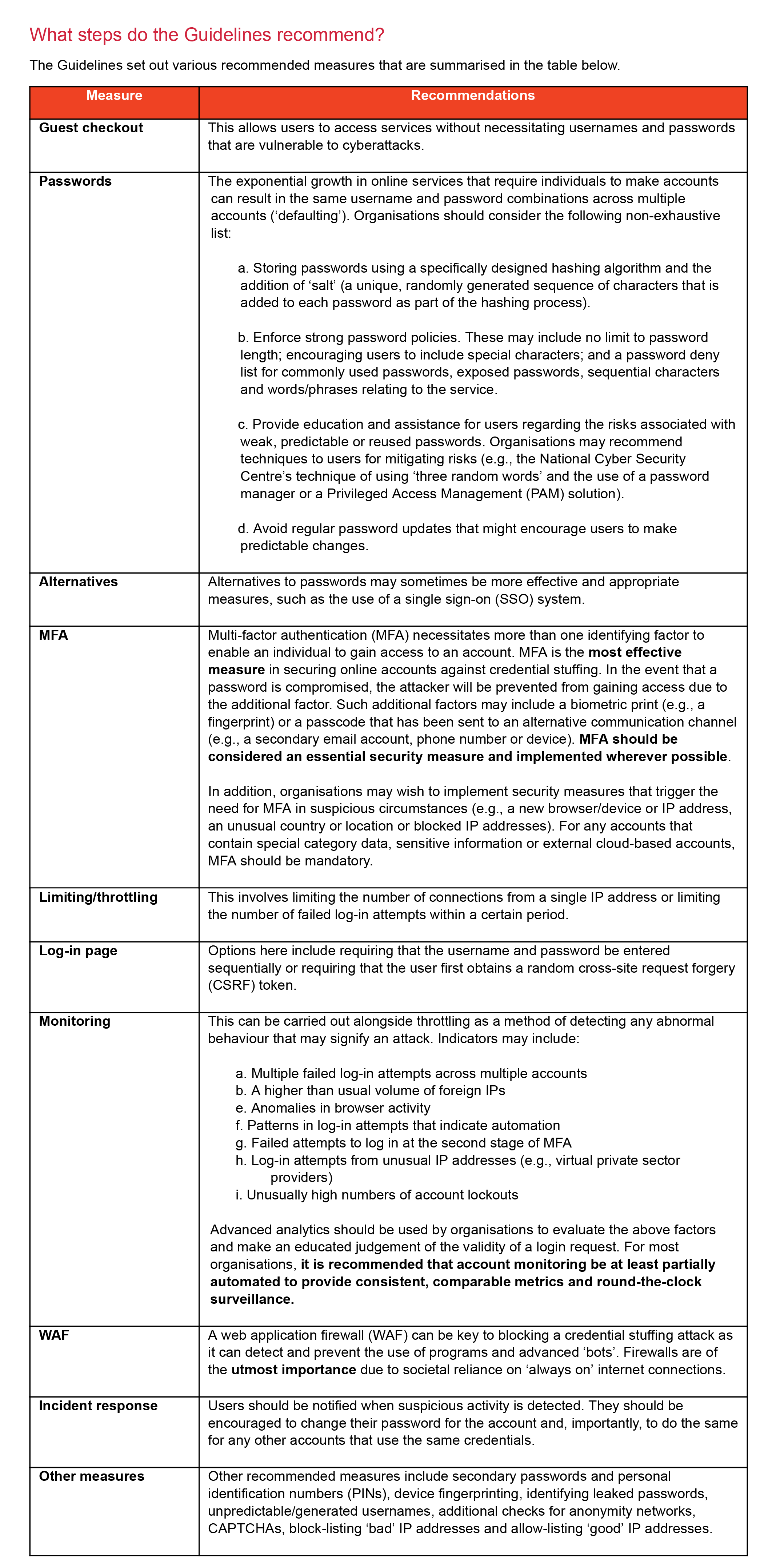
Given the general requirement around ‘appropriateness’, guidance on common security issues is therefore important to companies in determining the level of compliance that is required in practice. Whilst some guidance has been issued previously around password protection, there has not been practical targeted guidance around credential stuffing.
These Guidelines are not directly enforceable. However, they are already being referenced and publicised by regulators such as the Gibraltar Regulatory Authority and the UK Information Commissioner's Office. Following the Guidelines can therefore be useful for privacy law accountability purposes and, if personal data breaches trigger notification requirements, for confirming that recommended steps have been taken, which may either prevent further action being taken by regulators in the first place or at least be taken into account in assessing any compliance failures.
Client Alert 2022-229

