Authors
Key takeaways
- China has issued draft measures to impose stringent requirements on reporting of data incidents
- Significant business implications for MNCs and their business operations in China
- Business organisations are advised to take steps in response to enhanced compliance regime
In order to standardise the reporting of data incidents, reduce the losses and damage caused by data incidents, and maintain national cybersecurity, the Cyberspace Administration of China (CAC) released the draft Measures for the Administration of Cybersecurity Incident Reporting (Draft Measures) on 8 December 2023 for public consultation, with a closing date of 7 January 2024.
Reporting of cybersecurity incidents is not a new legal requirement in China. It is a provision of the Cybersecurity Law (CSL), the Data Security Law (DSL), the Personal Information Protection Law (PIPL), and other relevant legislation, but specific details are still lacking, and the legal provisions are not always consistent with each other. Once enacted, the Draft Measures will set out the specific requirements with respect to cybersecurity incidents and have a significant impact on business organisations. This client alert summarises the key requirements and highlights under the Draft Measures and discusses the major implications for business organisations.
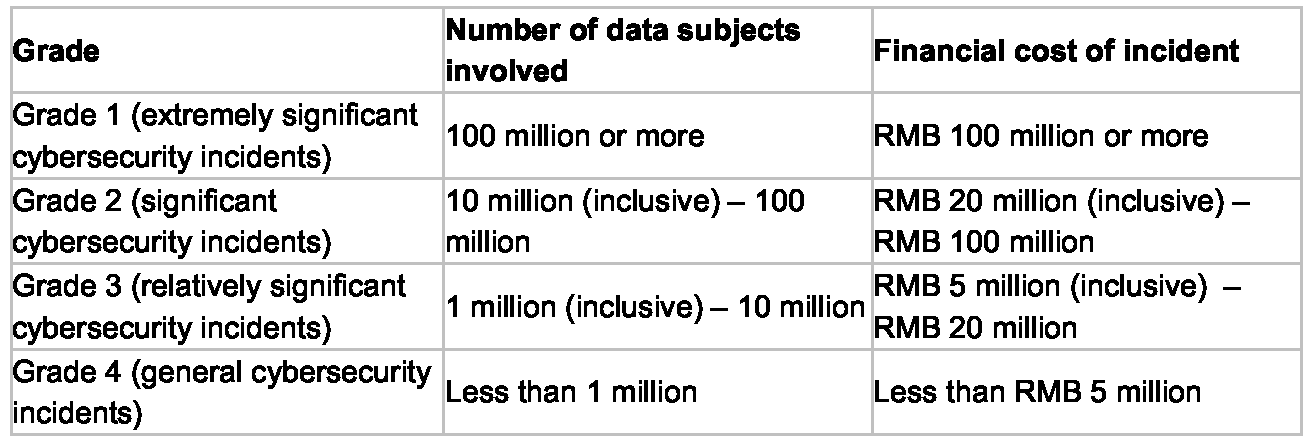
Grading of cybersecurity incidents
The Draft Measures provide specific criteria for each grade of cybersecurity incident based on various factors, including the level of the impact on national security and social stability, the duration of the incident, the financial losses as a result, etc. Below is an illustrative example of classification based on the number of data subjects involved and financial losses caused:
Scope of application
The Draft Measures apply to the reporting of cybersecurity incidents by network operators, who are responsible for building or operating networks or providing services through those networks in China. The scope of network operators is quite broad. Nowadays, almost all companies are considered network operators and are hence required to comply with the reporting requirements relating to cybersecurity incidents.
The Draft Measures are specifically applicable to cybersecurity incidents falling under Grade 1, Grade 2 and Grade 3. Grade 4 cybersecurity incidents are not covered by the Draft Measures and are hence subject to the general requirements under the CSL, the DSL and the PIPL. Grade 1-3 cybersecurity incidents will be subject to enhanced reporting requirements, while reporting on Grade 4 incidents can be relatively relaxed.
In light of the above, companies need to become acquainted with the criteria used to classify cybersecurity incidents so as to understand and evaluate which grade is likely to apply in case of any cybersecurity incident.
How to report
Each of the CSL, the DSL and the PIPL requires data handlers to take remedial measures and report to the regulator immediately after a cybersecurity incident occurs, but lacks detailed guidance. In contrast, the Draft Measures provide that Grade 1-3 cybersecurity incidents must be reported to the regulator within one hour. The regulator could be the local CAC, the public security bureau or the industry regulator depending on the nature of the relevant IT systems, business lines or other factors.
The Draft Measures provide a template form for reporting on cybersecurity incidents, covering the following required details:
- The name of the unit where the incident occurred and basic information about the facilities, systems and platforms involved.
- The time and location of the occurrence, the type of incident, the impact and damage caused, and the measures taken, as well as their effectiveness. For hacker attacks, the amount, method and date of the ransom should also be included.
- Details on how the incident evolved and possible further impacts and damage.
- Preliminary analysis of the cause of the incident.
- Indicators that require further investigation and analysis, including possible attacker information, attack paths, existing vulnerabilities, etc.
- Further response measures to be taken and requests for support.
- Measures taken to protect the incident site.
Among the above information, the Draft Measures emphasise that items (1) and (2) must be reported within one hour, with items (3) to (7) to be reported within 24 hours if not possible within one hour.
Under the EU General Data Protection Regulation (GDPR), the data breach must be notified to the supervisory authority within 72 hours after the controller becomes aware of it. The Draft Measures have proposed much more stringent timing requirements than the GDPR. In order to meet the stringent time frame, companies must establish a sound data breach response programme, get the response pack ready in advance, and train the relevant teams properly.
Law enforcement
The Draft Measures provide a range of mechanisms to monitor and encourage the reporting of cybersecurity incidents. If a vendor discovers that a cybersecurity incident has occurred involving its client while providing services, the vendor shall remind the client to report the incident to the regulator. The vendor may report the incident to the regulator directly if the client fails to do so. The public is also encouraged to report any Grade 1-3 cybersecurity incident to the CAC.
Violators will be subject to legal consequences according to the relevant provisions of the CSL, the DSL, the PIPL and other relevant legislation. Apart from the potential liability for the company (e.g., monetary fines of up to RMB 50 million), individuals responsible for cybersecurity incidents may face personal and even criminal liability.
However, the Draft Measures also provide that if the company has already adopted necessary and reasonable preventive measures, properly reported the cybersecurity incidents, and taken remedial measures according to the relevant emergency plans to minimise the impact, the legal liability may be exempted or mitigated.
In light of the above, it is of great importance to take all the required compliance actions and keep a close track of compliance efforts aimed at risk mitigation.
Practical considerations and next steps
Due to the exponential growth of digitalisation across industries, business organisations are increasingly vulnerable to cyberattacks and cybersecurity incidents. These threats can result in regulatory penalties, financial losses, interrupted business operations and reputational damage. The Draft Measures demonstrate a very clear trend of stricter law enforcement on reporting of cybersecurity incidents, indicating a need for stronger risk mitigation measures by companies for their operations in China. To address this, we advise the following compliance steps:
- Assess existing IT facilities, systems and platforms, and implement adequate and effective data security measures to safeguard information, communications systems and personal data based on the nature, scale and complexity of your data processing activities.
- Take a proactive approach by establishing a comprehensive emergency response plan for data breaches and cybersecurity incidents. This plan should outline steps for promptly notifying regulators and affected customers, designate responsible personnel for each step, and specify required response times, in compliance with applicable laws and regulations.
- Regularly monitor compliance with data security measures and periodically evaluate their effectiveness. Timely improvement actions should address non-compliant practices and ineffective measures.
- Proactively and regularly conduct cybersecurity training and organise emergency reporting drills for employees from time to time.
- Maintain a good record of all compliance efforts related to the cybersecurity incidents, documenting preventive and remedial measures taken, reporting documents, etc.
Client Alert 2024-004