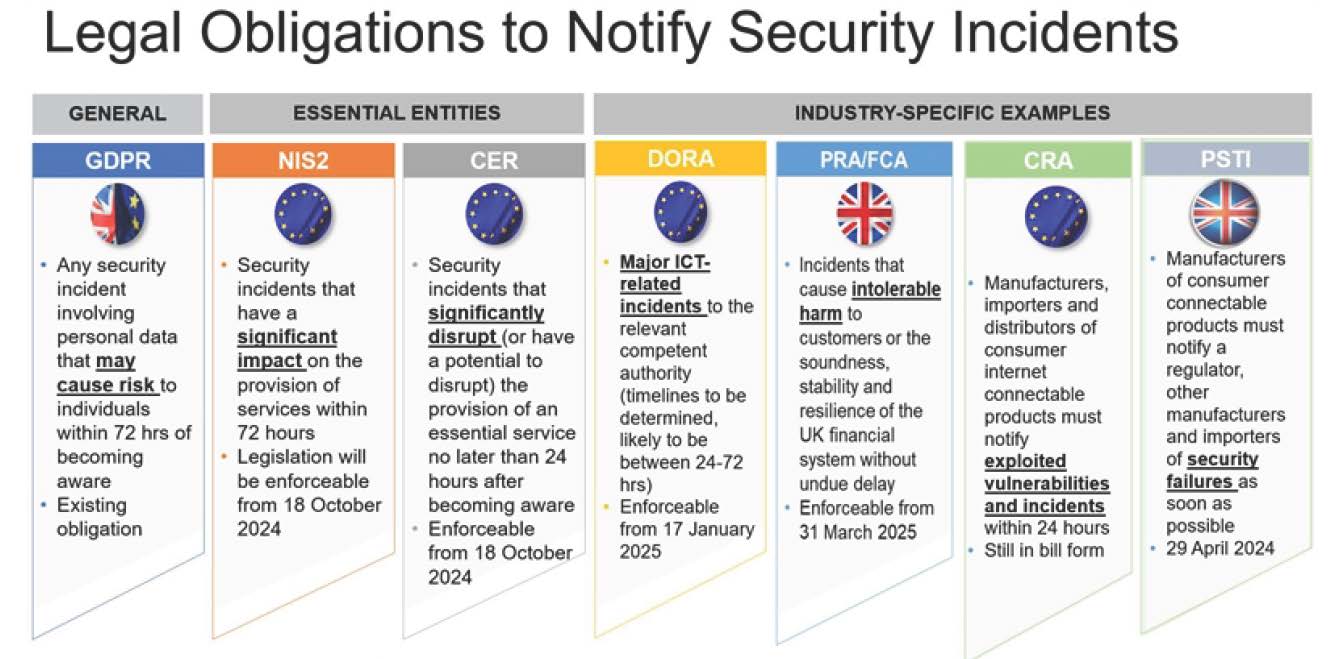
If you are subject to the new cybersecurity laws, it is time to update your incident response policies as the criteria for determining which cyber incidents to report to regulatory authorities or customers are changing. The graph below shows the changes to the notification obligation.
Existing obligation to report an incident
First, the graph shows the existing legal obligation to report an incident under the General Data Protection Regulation (GDPR) in the EU and the UK if it involves the personal data of individuals.
New obligations to report an incident
It also shows how the incident notification obligations under the new cybersecurity laws will affect organisations located or providing services in the EU that are (a) providing essential or important services under the Second Network and Information Security Directive (NIS2 – see our summary of the obligations) and/or (2) designated as critical entities under the Critical Entities Resilience Directive (CER – see a summary of the obligations).
Industry-specific requirements to report incidents
There are also new industry-specific requirements in relation to cybersecurity measures and incident responses. For example, both the EU and the UK require financial services organisations to implement operational resilience (including cyber resilience) measures under, respectively, the EU Digital Operation Resilience Act (DORA – see our updates) and the operational resilience rules published by the UK’s Prudential Regulation Authority (PRA) and Financial Conduct Authority (FCA) (PRA/FCA – see our summary).
Manufacturers, importers and distributors of consumer internet-connectable products may also be affected by the new obligation to notify consumers of exploited vulnerabilities and incidents within 24 hours, as set out in the EU Cyber Resilience Act (CRA), which is still in bill form. The UK is following suit and is expected to publish a proposal on a UK Cyber Resilience Act in the first half of 2024. This is in addition to the new UK Product Security and Telecommunications Infrastructure Act 2022 (PSTI) affecting manufacturers of consumer connectable products (smart TVs and internet-connectable devices), which will come into effect on 29 April 2024. It requires manufacturers to comply with minimum security requirements relating to passwords, report security issues raised with them by consumers, and carry out security updates.
Recommended steps
Step 1: Assess and document whether your organisation falls within the scope of the new cybersecurity laws
Assess whether the new cybersecurity laws apply to your organisation. We recommend documenting this assessment even if you decide that they do not apply, especially where your organisation is in an industry that is deemed to provide essential or important services and may face questions from a regulator or customer.
Step 2: Update incident response policies
a) Indicate the thresholds for notification of incidents
The new cybersecurity laws set different thresholds than the GDPR for reporting cyber incidents. Under NIS2, incidents (irrespective of whether they involve personal data) are notifiable only if they have a significant impact on services or significantly disrupt the provision of services (i.e., have caused or are capable of causing severe operational disruption to the services or financial loss for the organisation, or have affected or are capable of causing considerable material or non-material damage to others (individuals or organisations)). Significant disruption (or potentially significant disruption) to the provision of an essential service under CER depends on the number and proportion of users affected by the disruption, the duration of the disruption, and the geographical area affected by the disruption.
The operational resilience rules under industry-specific laws, such as DORA and the PRA/FCA, also set different thresholds for incident notification: the incidents must either be “major” or cause “intolerable harm”.
As for consumer internet-connectable products, notification to the competent authorities and consumers is required for serious cyber incidents and vulnerabilities.
If your organisation falls within the scope of the new laws, your incident response policies will need to clarify when the thresholds will be met under the laws. We still expect to see further clarifications, as well as guidelines, from regulators and lawmakers – we will keep you updated. For example, under DORA, the technical standards setting out the criteria for classifying incidents for notification purposes are expected to be reviewed and approved within the next few months.
b) Indicate the different timelines for notification
The graph shows that the timelines for notification also differ from the GDPR timelines depending on the nature of the incident and the services or devices it impacts. Your incident response policy should be tailored to the services within the scope of the new cybersecurity laws and clearly indicate that when an incident affects the services, the timelines under the applicable new cybersecurity laws will apply.
c) Indicate which regulator to notify
Although it has not yet been determined which regulators will be responsible for each of the new cybersecurity laws, there may be several regulators that will need to be notified of an incident covered by the laws, especially if your organisation provides services in several EU member states and in the UK. Your incident response policy will need to be clear as to the relevant regulators once this information becomes available.
Step 3: Train your staff and practise incident response under various scenarios
Once you have assessed whether your organisation is impacted by the new cybersecurity requirements and you have updated your internal policies in line with the requirements, train your personnel and carry out desktop incident response exercises to ensure your procedures work seamlessly.
The UK National Cyber Security Centre offers a free tool to test and practise a response to a cyber-attack: Exercise in a Box. If your organisation is large and sophisticated and requires a tailored approach to a desktop incident response exercise, we can assist with this.
Step 4: Update your contracts with the service providers
Ensure that any revisions to the cybersecurity standards that apply to your organisation’s services and products within the scope of the new cybersecurity laws are incorporated into your contracts with third-party service providers to ensure your organisation does not fall foul of legal requirements due to issues within your supply chain. Include contractual obligations requiring them to notify your organisation of any cyber incidents to ensure your organisation’s compliance with the new cybersecurity laws.
Client Alert 2024-082

