CAC security assessment
CAC released the Measures for Security Assessment of Cross-Border Data Transfer (Security Assessment Measures) on 7 July 2022 and the Guidelines on Application for Security Assessment of Cross-Border Data Transfers (1st Edition) (Security Assessment Guidelines) on 31 August 2022. Both came into effect on 1 September 2022. According to the Security Assessment Measures and Security Assessment Guidelines, a CAC security assessment is required for cross-border data transfers in any of the following circumstances:
- Cross-border transfers of important data
- Cross-border transfers of personal data by critical information infrastructure (CII) operators
- Cross-border transfers by data exporter processing the personal data of 1 million or more individuals
- Any transfer (in aggregate) of the personal data of more than 100,000 individuals or the sensitive personal data of more than 10,000 individuals that has occurred since 1 January of the preceding year
- Other situations requiring security assessment in accordance with PRC laws and regulations
In practice, the following issues should be taken into consideration for the purpose of security assessment:
1) Important data
“Important data” is defined as any data which may endanger China’s national security, economic operation, social stability, public health or public security, if it is tampered with, destroyed, leaked, or illegally acquired or used. The general principle for identifying important data is expected to be industry specific, department specific or region specific and will be further detailed by industry regulators and local authorities.
2) CII
CII is defined as “important network facilities and information systems” in the areas of public communication and information services, energy, transport, water conservation, finance, public services, e-government, national defence, and science and technology, as well as industries in which any damage, loss of function or data leakage may seriously endanger national security, the national economy and people’s livelihoods, or the public interest.
In practice, for those entities which have not been notified by the industry regulator as CII operator, it is highly likely that it will not be perceived as CII. However, it is still necessary to keep abreast of any changes to the definition of CII and communicate with the industry regulator from time to time on the current status.
Please note that Chinese regulators are in the process of finalising the regulations on determining important data and CII, and the final version is likely to be issued in the near future.
3) International data transfers
The Security Assessment Guidelines clarify that international data transfers from China include the following scenarios:
- An entity collects or generates data during its day-to-day operations in China and stores the data or transfers it abroad.
- A foreign entity outside China has remote access to (including being able to view, download, retrieve and export) data which is collected or generated during day-to-day operations in China and stored locally in China.
- Any other international transfer of data as determined by CAC at its discretion from time to time.
In practice, multinational companies often run shared IT systems or applications where the Chinese subsidiary shares, transfers or grants access to data collected or generated in China. This will be treated as a cross-border data transfer subject to mandatory security assessment if it falls under any of the above scenarios.
4) Documents, process and timeline
In order to initiate the security assessment process, the data exporter in China must work with the foreign data recipient to prepare a large volume of requisite documents, including the self-assessment report, the cross-border data transfer agreement, the application form and any other supplementary information depending on the specific requirements set out by CAC in the Security Assessment Measures and Security Assessment Guidelines.
The CAC security assessment takes about 60 working days, but this may be extended for complicated cases. Possible outcomes notified to the data exporter are that: (i) the assessment was not applicable, (ii) the assessment was passed and data transfer is allowed or (iii) the assessment was not passed and data transfer is not allowed. If the data exporter is not satisfied with the outcome of the CAC’s security assessment, it has the right to apply for a review, the result of which will be final.
The security assessment is valid for two years. The data exporter is required to submit a new assessment upon the expiry of the two year period or in the event of any change affecting data security, such as an extension to the data retention period, a change of control of the foreign data recipient, major changes in the destination country’s data laws and practice, and force majeure.
Any failure under a previous assessment to comply in full with the new rules must be rectified by 1 March 2023.
China SCCs
On 30 June 2022, CAC issued the draft Regulations of Standard Contracts for Cross-border Transfer of Personal Information (draft SCC Regulations), thereby unveiling the long-awaited terms of China SCCs. Under the draft SCC Regulations, a data exporter is allowed to transfer personal data abroad by way of the SCC mechanism if all of the following conditions are satisfied:
- The data exporter is not a CII operator.
- It has not processed the personal data of more than 1 million individuals.
- It has not made cross-border transfers of the personal data of more than 100,000 individuals (in aggregate) since 1 January of the preceding year.
- It has not made cross-border transfers of the sensitive personal data of more than 10,000 individuals (in aggregate) since 1 January of the preceding year.
The data exporter can only choose the SCC option if all the above criteria are satisfied; otherwise it must go through a security assessment.
The China SCCs share some similarities with the SCCs under the EU General Data Protection Regulation (GDPR). However, unlike the different modules (i.e., C-C, C-P, P-P and P-C) under the GDPR SCCs, China SCCs do not differentiate between scenarios based on the role of the parties. China SCCs also impose specific requirements, including the following:
- Chinese law shall be the governing law for cross-border data agreements and parties can only choose litigation at a court in China or arbitration proceedings at an arbitration tribunal in China or a member state of the 1958 New York Convention.
- The personal data protection impact assessment report and the signed SCCs must be filed with the CAC within 10 working days after the SCCs come into effect, although filing with the CAC is not necessary for the SCCs to come into effect or the China-based data exporter to transfer personal data abroad. However, it is worth noting that a failure to file according to the applicable rules may result in suspension of the cross-border data transfer.
Security certification
On 24 June 2022, China issued the Security Certification Guidelines on Cross-border Transfer of Personal Data (Security Certification Guidelines), which serve as the standard guidelines nationally. The Security Certification Guidelines apply to the intra-group cross-border transfer of personal data and processing of personal data outside China based on the extra-territorial application of China’s Personal Information Protection Law. An entity based in China, or any foreign data controller’s designated representative in China, can apply for security certification and assume the corresponding liability.
The Security Certification Guidelines share similarities with the BCR under article 47 of the GDPR. Either Security certification under the Security Certification Guidelines or the BCR is one of the mechanisms for cross-border data transfers that are applicable to and must be observed by all members concerned within the same group of companies.
The Security Certification Guidelines incorporate the fundamental principles and requirements applicable to security certification, serving as the basis for carrying out security certification and as compliance guidance for data controllers in the context of the cross-border transfer of personal data.
Security certification also requires a legally binding and enforceable agreement to cover the key terms and conditions of the processing of cross-border data transfers. In addition to the binding agreement, the relevant data controller and data processor must establish a data protection department, appoint a data protection officer, properly conduct a data protection impact assessment and formulate the rules with which the data controller and overseas data recipient must comply in the cross-border transfer of personal data . These rules are similar to binding corporate rules (BCR) , but have Chinese characteristics; for example, the BCR rules do not have to cover the identification of the third country or countries in question, but the Security Certification Guidelines require disclosure of such information.
The Security Certification Guidelines have not yet detailed the procedures for certification. We expect that more details on how to obtain certification will be provided in the near future.
Comparison of the three mechanisms and which one to choose
The three mechanisms are a significant part of the current cross-border data transfer regime in China.
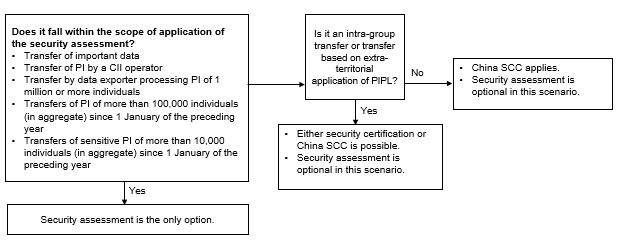
A security assessment is mandatory if any of the required scenarios is met. For instance, if a multinational company is a CII operator, or intends to transfer important data out of China, a security assessment will be the only option. The security assessment may take up to 60 working days or even longer to complete, and has three possible outcomes, which could present uncertainties for the intended data transfer. On the other hand, once passed, the security assessment is valid for two years and so can cover multiple data transfers to the same overseas recipient whilst valid.
As the equivalent in China of BCR under the GDPR, security certification applies to the intra-group transfer by the data exporter located in China. Once passed, security certification applies to all members concerned within the same group of companies. However, the detailed guidance on implementation of the security certification may require more clarity.
The draft SCC Regulations have not been finalised yet. The China SCC regime is expected to have clear advantages because of the greater predictability of contract terms and time/cost efficiencies. However, China SCC terms only apply if a compulsory security assessment is not triggered. Moreover, China SCCs are governed by Chinese law and must be filed with the CAC within the prescribed time. It could be challenging for overseas recipients to address the differences between the China SCC and their existing SCCs.
The following diagram illustrates the cross-border data transfer mechanism applicable in different scenarios:
Practical takeaways
Now that a new international data transfer mechanism is in place, business organisations are highly recommended to take appropriate compliance actions to facilitate cross-border data transfers. Although compliance requirements for each multinational company may vary on a case-by-case basis, the below requirements should serve as a general reference:
- Self-assessment to evaluate whether a cross-border data transfer falls within the scope of application of the security assessment, evaluating the best approach to cross-border data transfers, establishing a holistic and coordinated procedure for international data transfers and preparing the relevant documentation in the manner stipulated, e.g., a cross-border data transfer agreement and self-assessment report.
- Data mapping the China-related data inventory and data activities to understand the nature, category and volume of the data collected or generated by the business operation in China, and to establish whether any data is transferred from Chinese subsidiaries to the HQ/affiliates outside China and whether any remote access to the data collected in China has been granted to any overseas HQ/affiliates even if no China-collected data is stored or transferred abroad.
- Assessing the data exporter’s data security management capabilities and compliance with data privacy and cybersecurity laws. If any gap is identified, remedial measures have to be taken as soon as possible. Please note some remedial measures may be time-consuming. For instance, testing and filing under China’s multi-level protection scheme could take a few months and should be planned beforehand for risk mitigation purposes.
- Appointing a qualified data protection officer (DPO) in China if needed. Having a qualified DPO is helpful to optimise the data security management system and facilitate communication with CAC to mitigate non-compliance risks.
- Keeping a close watch on China’s legislative and enforcement developments and updating data-related documentation accordingly.
- Seeking professional legal and technical support in relation to data compliance strategy and establishment of a data security system.
In-Depth 2022-351

